A Structured Approach to Risk Management
Every enterprise faces risk—both known and unknown. Many organizations routinely assess risk, not only in the technology space, but also throughout the enterprise. And every day, enterprises seek to optimize risk, thereby ensuring the most advantageous return on investment while sustaining business continuity. Risk changes almost daily, and IT security leaders are effectively forced to identify and address threats and vulnerabilities continuously to prevent exposure of important data and maintain risk tolerances at acceptable levels.
Risk assessments allow the enterprise to reevaluate existing and potential risk within structured, repeatable frameworks that inform the organizational risk response. In dynamic and evolving risk environments, enterprise information and technology assets depend upon robust risk-assessment methodology and planning, not only to secure the assets themselves, but also to understand and appreciate their full institutional value, to identify business processes that rely on them, potential options for mitigation, and criticality and priority of any associated risk items relative to organizational risk appetite.
Risk is defined as combination of the probability of an event and its impact. For risk to exist, there must be a chance that some event or deviation from the norm will produce an unknown or unexpected positive or negative outcome.
Risk is a part of every enterprise’s daily operation. Risk comes in different forms, and can cause varying degrees of disruption and damage or alternatively, return varying rates of business value. Risk tends to increase over time as a result of increasing complexity. The best way for enterprises to prepare for and address possible security threats is to create a risk assessment strategy and plan that not only complement, but also champion enterprise goals. While no plan can eliminate risk, steps can be taken to reduce risk and mitigate the damage it can cause.
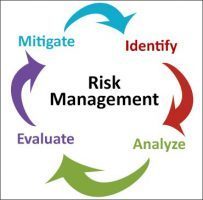
All enterprises should have some form of risk assessment in place to account for both current and future threats. Such assessments not only provide a basis for determining the value of business assets and the impact of security breaches, but also promote the overall security and stability of the enterprise on an ongoing basis. There is no one right way to conduct a risk assessment. However, it is generally agreed that risk assessment should adhere to a structured methodology. The most common steps include:
- Identifying and valuing assets
- Identifying known threats
- Identifying vulnerabilities
- Identifying risk
- Determining the risk treatment
Across these steps are the key aspects of a risk assessment that determine its success and overall usefulness to the organization. Critical considerations include:
- Identifying and prioritizing assets based on their value
- Identifying threats and vulnerabilities
- Analyzing controls in a structured, repeatable manner
- Determining the likelihood of incidents
- Assessing the impact of incidents
- Promoting communication and collaboration among IT security teams and organizational management.
In some instances, other key stakeholders may need to be consulted. Recording risk events in a risk register is recommended for documenting each step of a risk event both for historical purposes and to plan ahead.
Conclusion
A structured IT security risk assessment enables an enterprise to identify, evaluate and align its overall security position with its risk appetite. Assessments provide the opportunity for staff to work across functional areas and promote communications among IT teams, security managers and upper management, contributing to a broader understanding of how processes and assets interact. All of these insights benefit senior managers who seek to conduct operations while maintaining an acceptable level of risk.